Cybercriminals are increasingly targeting VMware ESXi hypervisors, exploiting SSH tunneling for persistent access and ransomware deployment. If your server has any virtual machines, there’s a good chance you’re using ESXi! These systems, crucial for virtualization, are often under-monitored, making them prime targets.
The Threat: ESXi Hypervisors Under Attack
ESXi hypervisors are critical components in virtualized environments, often hosting multiple virtual machines on a single server.
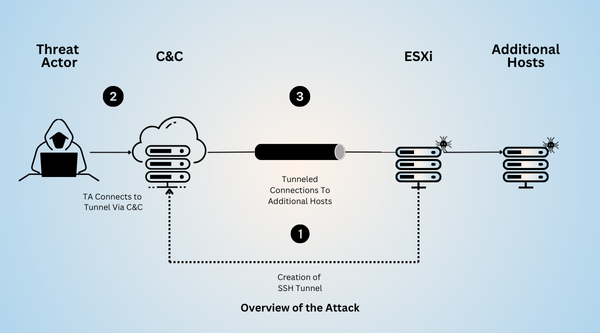
Attackers gain access through various means, including exploiting vulnerabilities or credentials. Once inside, they abuse ESXi’s built-in SSH service – intended for legitimate remote administration – to establish persistent connections. This allows them to:
- Maintain a Hidden Presence: SSH tunneling creates covert backdoors, often undetected due to the continuous uptime of ESXi appliances.
- Move Laterally: Attackers can use these tunnels to navigate deeper into the network, compromising additional systems.
- Deploy Ransomware: The ultimate goal is often ransomware deployment, encrypting critical data and crippling operations.
Detecting these attacks is challenging due to ESXi’s distributed logging.
IT Security Awareness 2025 Lunch and Learn
Join our first virtual Lunch and Learn of 2025! IT Security 101 has been updated with new tips for new security threats in the new year. Plus, we’ll treat you to lunch with a $20 Grubhub gift card!

- Date – Wednesday, February 12th
- Time: 11:00am – Noon
- Location: Virtual
- Topics Covered
- Phishing Prevention
- Social Media Scams
- AI Threats
- MFA – No Longer Optional
- & Much More!
