Last week, Trend Micro detected PowerShell scripts that were downloading ENTSCRYPT (GermanWiper), a ransomware variant that makes file retrieval impossible. The malicious scripts are delivered through spam emails containing a Zipped file with embedded LNK, which overwrites the content of local files with zeros and changes the file extension to 5 random characters.
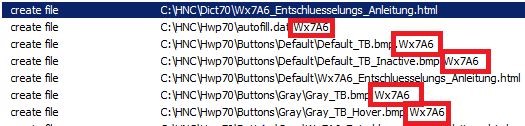
When complete, ENTSCRYPT opens a ransom note in German requesting US $1,500 Bitcoin in exchange for a decryption key.
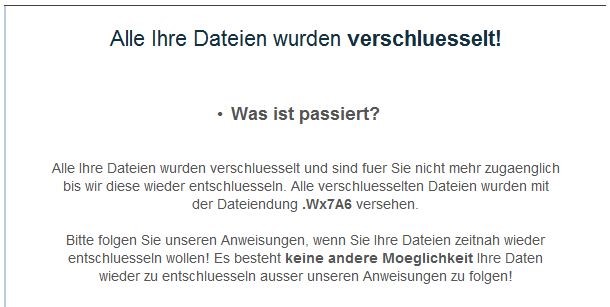
Since the contents were overwritten with zeros, decrypting results in worthless files containing nothing but “000000000…”, which has motivated some municipalities to adopt a “we don’t pay ransoms” policy.
Trend Micro recommends the following defensive steps:
- Watch your inbox for suspicious emails with URLs or attachments inside, and avoid clicking on URLs or attachments.
- Verify your data backups to make sure you have adequate storage and recent backups have completed without error. It’s always a good idea to perform a trial restore of files in various folders.
- Restrict access to important data and administration tools, and use group policy to automate and enforce access controls.
- Keep your firmware and operating systems updated with available patches, and be sure to upgrade operating systems and devices prior to EOS (end of support). Example, Windows Server 2008 and Windows 7 both go EOS on January 14, 2020, so start your upgrade planning now.
On July 29, 2019, US CISA (Cybersecurity and Infrastructure Security Agency) released a newsletter recommending immediate action to safeguard against ransomware attacks.
- Backup (now & daily) all critical business and system configuration information, verify the integrity and it’s ability to restore, and keep the backup on a separate device with an offline copy as well.
- Train and re-train employees on recognizing threats and phishing emails, and on the importance of reporting anything suspicious.
- Create an Incident Response Plan to address attacks, what to do when internal capabilities are overwhelmed, how to request assistance and from whom, and keep handy a paper list of state agencies like CISA in case of attack.
CISA gives a few more recommendations in their Ransomware Tip Sheet:
- Restrict employees’ permission to install software.
- Application-whitelist approved programs, and blacklist everything else.
- Use strong email spam filtering to detect threats and remove executable files.
- Block known malicious IP addresses and geo-fence off certain geographies.
Many US federal agencies collaborated and published How to Protect Your Networks from Ransomware that adds more important tips:
- Build awareness and train employees to watch out for and recognize phishing.
- Configure automatic disabling of macros embedded in Office files received or sent through email.
- Categorize data based on it’s value to the organization, and use physical and logical segmentation of networks and data for each organizational unit.
- Conduct periodic penetration testing using a qualified service provider.
- Backup, then secure those backups in the cloud or physically off-line behind lock and key.
Your best defense against ransomware continues to be an informed and watchful human firewall, and in case something does get through, you need quality backups completed prior to an event. Contact LeeShanok for a confidential discussion of your situation and strategies.
Your Technology Partner,
The LeeShanok Team
Tucson: 520.888.9122
Phoenix: 602.277.5757
