A sophisticated new phishing campaign has been discovered that imitates two of the biggest tools used by businesses: Indeed and Microsoft 365. The campaign is very difficult to detect, so we need to stay educated and vigilant, even when things “look” right!
Attack Details
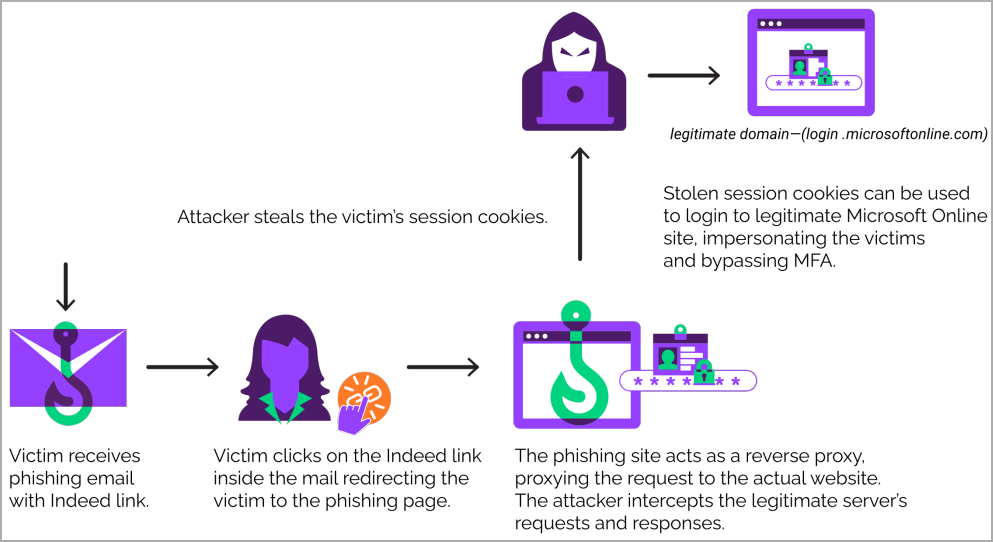
The threat actors leveraged an open redirection vulnerability on the job search platform Indeed. The link looks safe because it appears takes victims to Indeed.com. However, it actually redirects them to a phishing site impersonating Microsoft.
This is a classic example of an Adversary In The Middle (AiTM) phishing attack. The hackers use a reverse proxy to harvest session cookies, thereby bypassing multi-factor authentication (MFA). Ultimately, the hackers’ goal is to take over the email accounts of top-level executives.
How to Stay Safe
To catch this threat, you’d have to spot two easily-missed phishing email signs:
- The sender’s email address was NOT actually from an @indeed.com account
- The redirect instructions buried DEEP in the URL (i.e. indeed.com/example1random2text3&target=http://phishingsite.com/…)
Where could you and your team learn helpful tips like those…?
Join Our NEW Security Training Webinar Meet The Hackers!
We’re combining the practical tips from Security Awareness 101 with real world, fascinating examples of the tricks hackers are using to breach your systems. Attendees will enjoy lunch on us with a $20 Grubhub Gift Card after the presentation!

Date: Thursday November 2nd
Time: 11AM – 12PM
Location: Virtual
Topics Covered:
- Social Media Attacks
- Social Engineering
- Phishing Attacks
- Phone Scams
- & Much More!
