A Journey Through Time: Understanding The Evolution Of Cybersecurity Threats
Imagine the early days of computers. People were excited to explore this new technology, but they didn’t realize the dangers lurking beneath the surface. Just like in any new frontier, there were those who sought to use technology for harm.
This is the story of cybersecurity and the evolution of cybersecurity threats– a constant battle between those who seek to protect, those who seek to exploit, and some of the biggest cyber catastrophes experienced by millions of people over the past 45 years.
The 1980s: The Dawn Of Digital Danger And The Evolution Of Cybersecurity Threats
The 1980s marked the beginning of this digital arms race. People were starting to connect computers to each other, and with that came new risks.
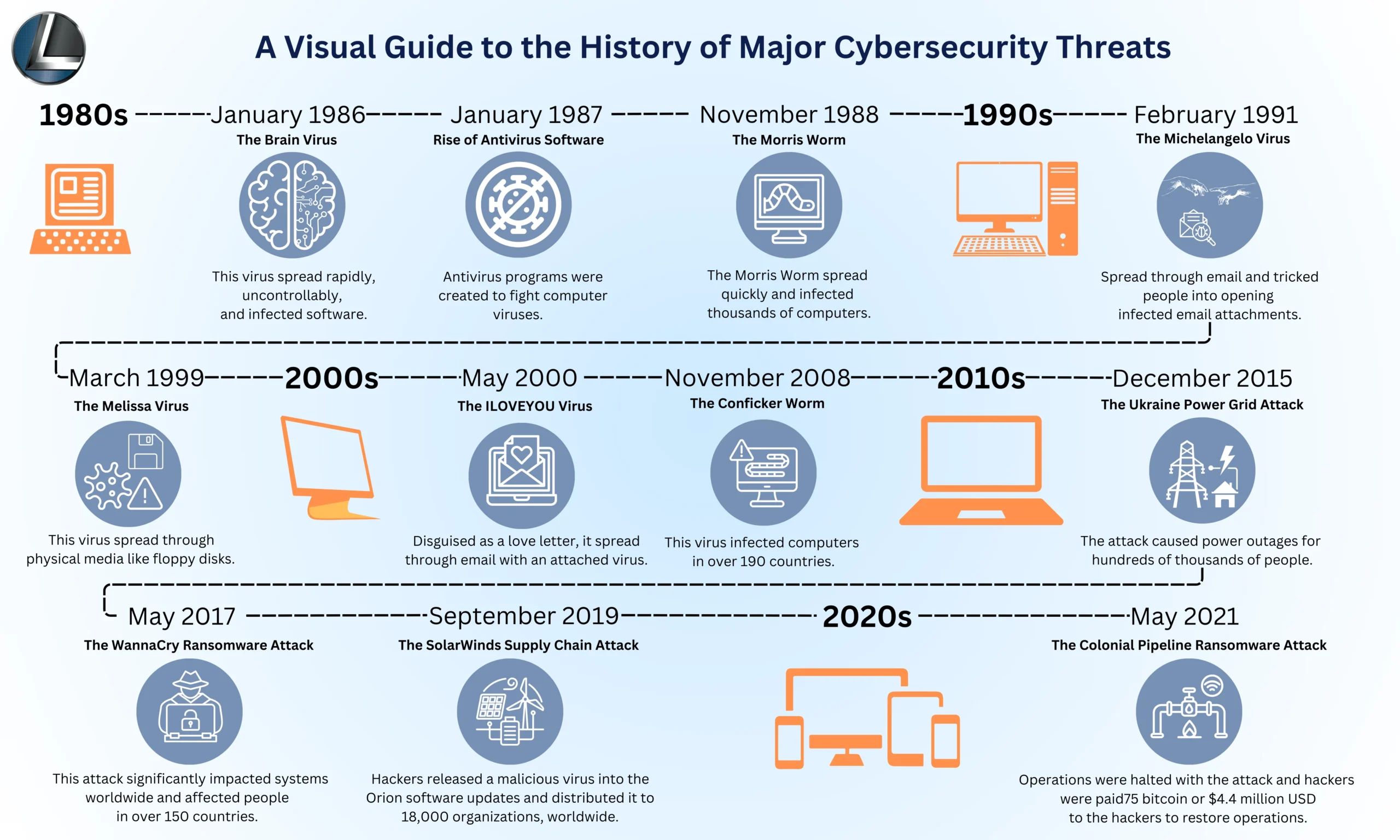
- November 1988 – The Morris Worm: This was a major turning point. The Morris Worm was a program that could spread rapidly across the internet, infecting thousands of computers. It demonstrated the speed and scale at which problems could spread in this interconnected world.
- January 1986 The “Brain” Virus: This was a historic moment. Two brothers in Pakistan created this virus to protect their software, but it ended up spreading uncontrollably. It was a wake-up call, showing us that even things meant to be helpful can have unintended consequences in the digital world.
- The Rise of Antivirus Software: As viruses started to appear, people began developing tools to fight back. Programs like McAfee VirusScan emerged, marking the beginning of a continuous struggle between those who create security software and those who try to bypass it.
Key Takeaway: The 1980s taught us a crucial lesson; connecting computers together comes with inherent risks. We needed to be aware of these risks and start thinking about how to protect ourselves.
The 1990s: The Internet Takes Off, And So Do The Threats
April 23, 1993, the dawn of the Internet for the everyday public; would soon explode in popularity. This was a fantastic time for communication and innovation, but it also opened the door for cybercriminals to spread their influence, and where the evolution of cybersecurity threats became more mainstream.
- March 1992 – with the emergence of the Michelangelo Virus. This pre-internet era virus, designed to activate on its creator’s birthday, was a boot sector virus. Such viruses primarily spread through physical media like floppy disks or USB drives. When a computer boots from a disk containing the malware, the virus infects the system, becoming active upon loading.
- March 1999 – The Melissa Virus: This virus spread through emails, tricking people into opening infected attachments. The Melissa Virus highlighted the importance of being cautious with emails and attachments, even if they seem to come from someone you know.
Key Takeaway: The 1990s showed us how quickly problems can spread across the internet. Cybercriminals learned how to exploit the growing interconnectedness of our world to their advantage.
The 2000s: Bigger Breaches, Bigger Problems
The 2000s brought more sophisticated threats and more serious consequences.
- May 2000 – The ILOVEYOU Virus: This virus, disguised as a love letter, spread rapidly through email, causing significant damage to computers worldwide. It served as a stark reminder of the dangers of opening emails from unknown senders.
- November 2008 – The Conficker Worm: This worm infected millions of computers, demonstrating the potential for widespread disruption. It also emphasized the importance of keeping our software updated with the latest security patches.
- The First Major Data Breaches: The 2000s also saw the emergence of major data breaches. The CardSystems breach, for example, exposed millions of credit card numbers, highlighting the importance of protecting sensitive information.
Key Takeaway: This period showed that these threats weren’t just a nuisance; they could have serious financial, personal, and even societal consequences.
The 2010s: Ransomware And State-Sponsored Attacks
The 2010s marked a significant shift where data breaches, major attacks, and ransomware became substantial threats.
- December, 2013 – The Target Data Breach: This breach compromised the personal information of millions of Target customers, demonstrating the importance of robust security measures for businesses.
- December 2015 – The Ukraine Power Grid Attack: This attack demonstrated the potential for cyberattacks to disrupt critical infrastructure, raising serious concerns about national security.
- May 2017 – The WannaCry Ransomware Attack: This Wanna Cry attack crippled computers worldwide, highlighting the devastating potential of ransomware and the need for rapid response capabilities.
- September 2019 – The SolarWinds Supply Chain Attack: This attack demonstrated the vulnerability of the software supply chain, showing the need for heightened security measures throughout the entire software development and distribution process.
Key Takeaway: This period showed that cybersecurity was no longer just about protecting individual computers. It had become a matter of national security and critical infrastructure protection.
The 2020s: The Rise Of AI In The Evolution Of Cybersecurity Threats
Today, the evolution of cybersecurity threats has led to attacks more sophisticated than ever before. Cybercriminals are now using artificial intelligence (AI) to make their attacks more targeted and effective.
- May 2021 – The Colonial Pipeline Ransomware Attack: This attack crippled a major fuel pipeline, demonstrating the real-world impact of cyberattacks on critical infrastructure and the economy.
- The Rise of AI-Powered Attacks: In the coming years, we can expect to see even more sophisticated attacks powered by AI. These attacks will be harder to detect and respond to, requiring constant improvement in cybersecurity defenses.
Key Takeaway: The cybersecurity landscape is constantly evolving. We need to be prepared for new and emerging threats, and we need to continuously adapt our defenses to stay ahead of the curve.
Lessons Learned And Looking Ahead
The history of cybersecurity teaches us several crucial lessons:
- Proactive Defense is Crucial: We can’t wait for problems to happen. We need to be proactive and implement strong security measures, such as firewalls, antivirus software, and regular system updates.
- Vulnerability Management Is Key: Many attacks exploit known vulnerabilities. Regular security assessments and timely patching are essential to minimize risk.
- Invest in Recovery and Resilience: We need to have plans in place to recover from attacks, such as data backups and disaster recovery strategies.
- The Human Factor Matters: Educating employees about cybersecurity best practices, such as recognizing phishing emails and creating strong passwords, is crucial.
The digital world is evolving, and so are cyber threats. From ransomware to social engineering, attacks are growing more sophisticated. Understanding past attacks is key to defending against future ones.
LeeShanok Network Solutions helps you navigate this complex landscape. We leverage historical analysis and stay ahead of emerging threats to provide robust cybersecurity solutions, including strong passwords, multi-factor authentication, and regular updates. Secure your digital future with LeeShanok.

Copyright © leeshanok.com
Website by CS Design Studios